|
|
|
|
 |
|
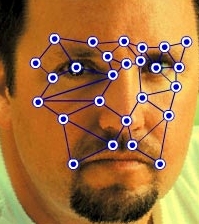
Biometrics is a process of
identifying a person by their
unique and measurable human
characteristics. |
|
A
personís biometric
characteristic can be the size
and shape of a hand, the ridge
and valley pattern of a
fingerprint, the frequency of
voice or iris characteristics of
the eye. |
|
No longer are
these devices found only in
James Bond movies and Star Trek
reruns. They are used on the
front door of thousands of
businesses around the world.
More advanced technologies
coupled with affordable
components and the demand for
high security have allowed
biometrics to become a common
component in the commercial
access control landscape. |
|
|
|
Today, thousands of businesses use biometrics.
At ASI we design and install Biometric solutions
that fit your current security needs, while
taking into consideration the needs that may
arise in the future. Organizations
are beginning to see the benefits of biometric
identity and access control management.
|
 |
|
Some of the
different types of biometric
solutions available are
fingerprint recognition, face
recognition, iris recognition,
hand geometry recognition, voice
recognition and finger print
recognition.
|
|
 |
|
|
Integrated Access Control |
 |
|
Access control is the process by
which users are identified and
granted certain privileges and
access to information, systems,
resources and entry into certain
areas of a building or facility.
Access control devices properly
identify people, and verify
their identity through an
authentication process so they
can be held accountable for
their actions. Good access
control systems record and
timestamp all communications and
transactions so that access to
systems and information can be
audited at later dates. Access
control systems provide
authentication, authorization,
and administration. |
|
|
|
There are different types of access control
technologies that can all be used to solve
access solutions. Proximity keys, smart cards,
and passwords are some of the more popular
access control technologies. Access control
systems can be used to control access to
computer data bases, server rooms, facility
entry doors, interior departmental doors,
turnstiles and more. |
|
|
|
 |



